IMAGE PROCESSING: Iris recognition system uses dual FireWire cameras
To measure the characteristics needed to verify a person’s identity, biometric identification (ID) systems can use fingerprints, retinal and iris scanning, hand geometry, voice patterns, and facial-recognition techniques. However, according to tests conducted by British Telecommunications, the unprecedented false match rate associated with iris recognition is far higher than for any other known biometric technology.
Pioneered by John Daugman at the University of Cambridge’s Computer Laboratory in 1991 (see “Wavelet analysis ensures accurate recognition of iris patterns,” Vision Systems Design, November 1999), Daugman’s algorithms now form the basis of almost all current commercially deployed iris-recognition systems, including the recently introduced Iris on the Move (IOM) system from Sarnoff (Princeton, NJ, USA; www.sarnoff.com).
Unlike many other commercially available systems that require subjects to stop and stare directly into a scanner for a set period of time, the IOM verifies identities by scanning irises from a distance of 3 m, allowing subjects to move through security checks at speeds of up to 30 people per minute (see Fig. 1).
To accomplish this task, engineers at Sarnoff combined a number of seemingly disparate technologies including near-infrared (NIR) illumination, dual FireWire cameras, and off-the-shelf image and iris recognition software.
“As a subject approaches the scanner,” says Ray Kolczynski, product manager of the IOM system at Sarnoff, “a sensor is used to trigger two banks of NIR LEDs mounted on either side of the scanner. Each of these LED banks is composed of an array of 12 × 12 individual LEDs mounted to illuminate the upper half of the subject’s torso.”
Because these LEDs operate at 850 nm, the illumination is imperceptible to the human eye and is not distracting to the subject moving through the scanner. “To capture an image of the subject’s iris,” explains Kolczynski, “the approximate position of the person’s eyes must first be located within the field of view of the scanner.”
To accomplish this, a multicamera system is employed to capture an image of the upper torso. This image is then transferred to the host PC running a combination of commercial and custom software. Using this software, the system locates the position of both the subject’s eyes within a region of interest. “Because we use a camera with a 2448 × 2048-pixel image sensor,” says Kolczynski, “we are able to capture a high-resolution image of the area around the person’s eye.”
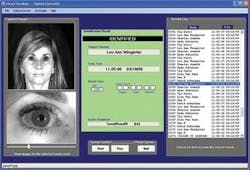
After images of the region of the eye are captured at high-resolution, they are again transferred to the host PC. To analyze the iris pattern within the image, the IOM system incorporates IrisAccess software from LG Electronics Iris Technology Division (Cranbury, NJ, USA; www.lgiris.com), software that incorporates the original algorithms proposed by Daugman (see Fig. 2). The system is agnostic and can work with all leading iris-matching algorithms.
According to Kolczynski, Sarnoff’s IOM system has already seen a number of deployments in military facilities and airports. In March 2009, the IOM system was one of three systems chosen for evaluation at Amsterdam’s Schiphol Airport. The airport is testing all three systems in a closed testing environment to understand how different biometric ID technologies work.
Although the technology has been primarily developed for iris recognition, it’s easy to envision a similar concept used as the foundation for other applications. At secure military trade conferences, for example, it may be necessary to rapidly identify a person’s barcoded badge and store their information in a database. By pairing a high-resolution camera with pattern-recognition software that can spot a logo or insignia on a badge, it would be possible to create an automatic, rapid pass-through system for this type of identification. In theory, all it would take is a few tweaks in optics and a different back-end processing system.